Windows Update for Business (WUfB) and Update Compliance

Windows Update for Business (WUfB) is a free service which allows you a level of control over Windows Update on certain SKU of Windows 10 - Pro/Enterprise/Education/Pro for Workstation - basically everything except Home edition. You can select which types of updates you would like - Feature updates, Quality (security) updates, Driver updates and Microsoft Product updates. Product updates are for other Microsoft products, but not Office if you used the Click-to-Run installer.
Whilst you don't approve/deny each update as you'd have done in the past with WSUS, you can specify update deferral periods. For Quality updates this is 30 days or less, and for Feature updates it's 365 days or less. You can create multiple policies, for example one targeting a pilot group with 0 day deferral, one with 5 day for a wider group, and a 10 day deferral for the rest of your devices. If you find an issue with an update installed by the pilot group, you can pause updates for up to 35 days on the other policies. The devices should then resume at the end of the 35 days and skip the missed update, moving on to the next cumulative update.
Device driver updates are enabled by default, but can be turned off, and Microsoft Product updates are disabled by default, but can be turned on. I tend to leave these at the default settings - as the trend with recent Microsoft products has been for them to look after the updating process themselves (e.g. Office 365 Click-to-Run, Edge etc) rather than using Windows Update.
You don't need Intune or Config Manager for this, and you don't need your devices to be Azure AD joined - it can even be a PC in a workgroup - although it's a lot easier to manage if you have some central control over the client side settings.
Configuring Policies
Windows Update for Business policies can be configured in a few ways. Obviously just pick one rather than having multiple policies fighting each other, unless you've got a split deployment e.g. some devices on Config Manager and others which are only managed by Intune.
If you're replacing WSUS in your environment you'll need to make sure that your device are no longer configured to update from the WSUS server and instead to update directly from Windows Update. It's also worth configuring Delivery Optimisation to cut down on bandwidth usage by the update services. I usually have this set to allow updates from the Windows Update servers and local clients behind the same NAT.
Endpoint Manager (Intune)
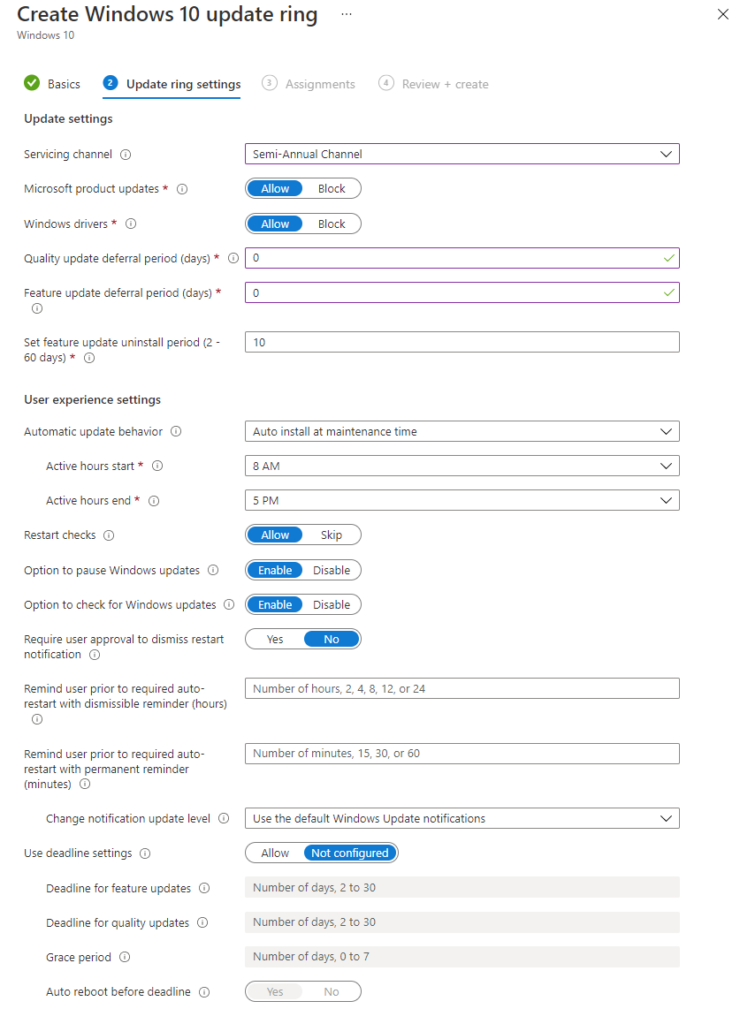
To configure the policies for Endpoint Manager, you'll need to go to Devices > Windows 10 update rings. You can create as many policies as you like, each targeting different groups. This way you can pilot updates on a small set of devices by giving them a 0 day update deferral, before they automatically update on other devices with a 2 or 5 day deferral, or whatever suits your environment.
If you need to pause updates, you simply click onto your policy, then on the Overview screen you have the option to Pause. This is much easier to get at than the Config Manager and Group Policy versions.
Config Manager
Similarly to Intune, you can create as many policies as you like in Config Manager and deploy them to the relevant device collections. From the console, go to Software Library > Windows 10 Servicing > Windows Update for Business Policies, and create a policy. You don't have as much control here as you do on the Intune version but you can still set the update branch and set any update deferrals.
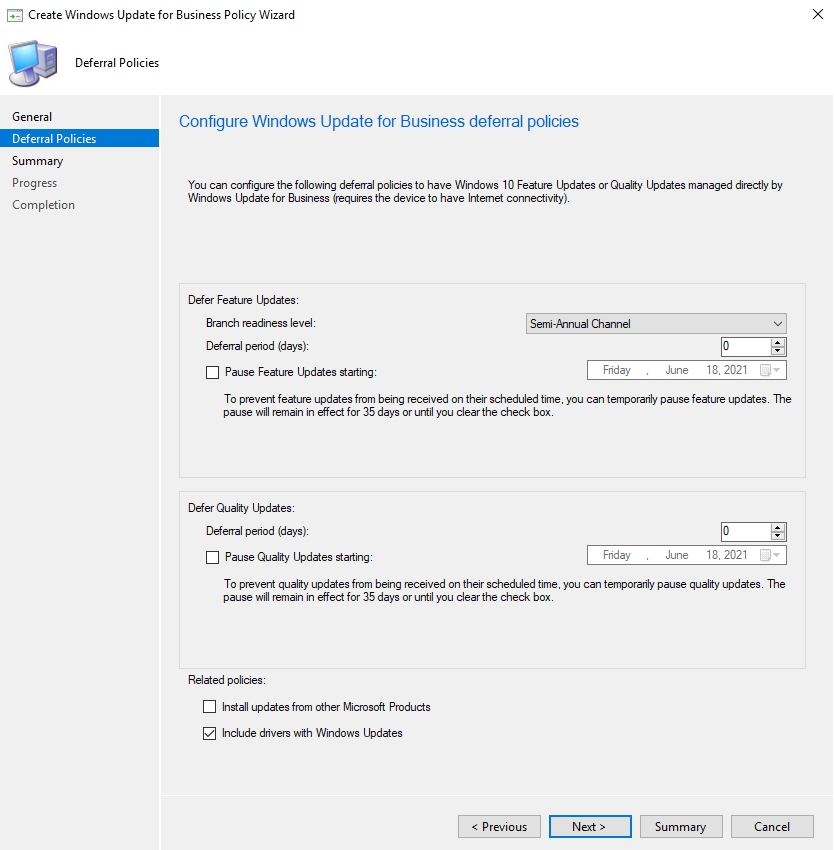
If you need to pause updates, you can do so by editing the properties of your update policy.
Group Policy
You can also manage these settings using Group Policy. Make sure Windows Updates are configured to download straight from Microsoft and configure the Quality and Feature Update delays.
Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update > Windows Update for Business.
If you need to pause updates, you can do that through one of the policies in this section.
There's a lot more control using Config Manager or Intune so I'd recommend those over the Group Policy method.
Monitoring Update Compliance
Now that we have our devices updating from Windows Update, we need a way to determine whether they are actually working or not. Previously we would have done this through WSUS and had a look at the console, we can still view similar data with WUfB however we have to take care of a few things to set up Update Compliance.
Creating the Log Analytics workspace and WaaSUpdateInsights Solution
If you have already set up Desktop Analytics, you're halfway there as you need to use the same Log Analytics workbook for Update Compliance and Desktop Analytics, with the same CommericalID and telemetry settings. If you've done this, you can skip the creation of the Log Analytics workspace.
First of all we need to create a Log Analytics workspace. Go to the Azure Portal > Log Analytics and click Create. Select your subscription, resource group (or create a new one), and the name and region you would like, and click Create.
Next we need to go to Update Compliance, which can be found in the Marketplace. You'll be asked to select your Log Analytics workspace (the one we just created, or if you already have Desktop Analytics then use that one) and then click Create. After a few moments you should see "Microsoft.WaaSUpdateInsights" was successfully deployed. Open the resource - if you've lost it, search for Log Analytics workspaces, and go through your workspace > solutions > WaaSUpdateInsights.
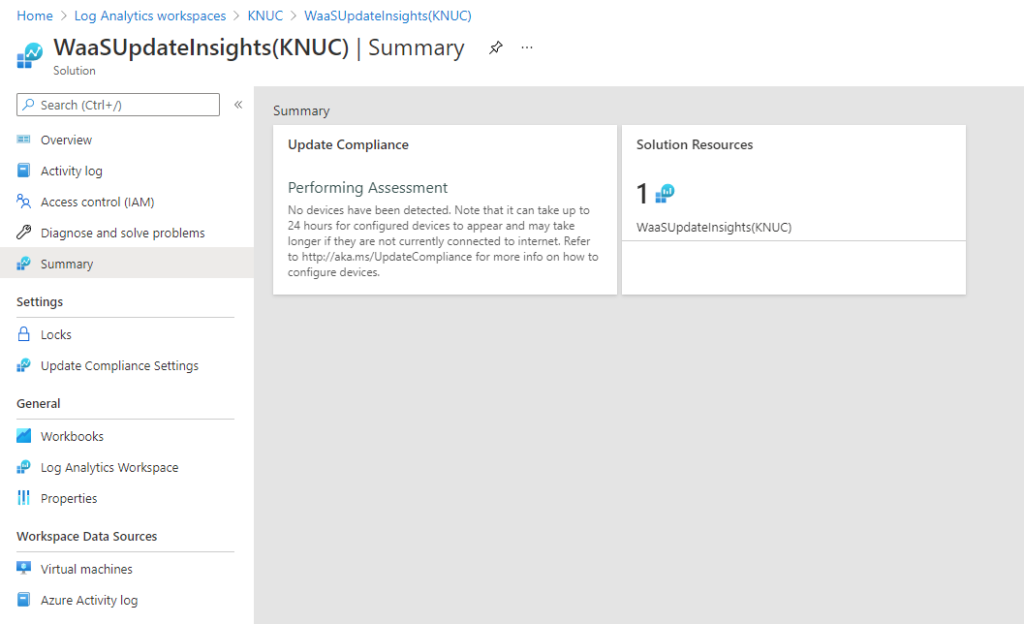
We now need to get the CommericalID. Click on Update Compliance Settings in the navigation bar, and copy the CommercialID shown - it should look like a GUID.
Configuring Devices
If you've got Desktop Analytics configured and your devices are appearing in it, you won't need to do anything to configure your devices for Update Compliance as it's the same deal - CommercialID, telemetry etc.
This can be configured by registry setting, Group Policy, a configuration script or through Intune. You can find details on the script here: Update Compliance Configuration Script - Windows Deployment | Microsoft Docs
Registry or Group Policy Method
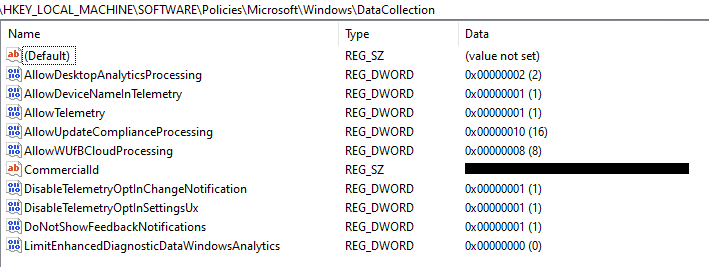
I've put the GPO Setting and Registry settings into a table along with notes describing what they do. The Group Policy settings are in Computer Configuration > Policies > Administrative Templates > Windows Components > Data Collection and Preview Builds, and the registry settings are in HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection. These GPO settings directly control the registry settings so you only need to do one of these. I've included the registry setting list incase you wanted to configure this through Config Manager, perhaps through a compliance/configuration baseline item.
| GPO Setting | Registry Setting | Notes |
|---|---|---|
| Allow device name to be sent in Windows diagnostic data=Enabled | AllowDeviceNameInTelemetry=1 | Needed to show device names, otherwise they show as # |
| Allow Telemetry=Enabled, 1 (Required) or 2 (Enhanced) | AllowTelemetry=1 or 2 | Configures telemetry level, needs to be either Basic or Enhanced. |
| Allow Update Compliance Processing=Enabled | AllowUpdateComplianceProcessing=16 | Opts the device into Update Compliance |
| Configure the Commercial ID=(Your Commercial ID) | CommercialId=(Your Commercial ID) | Sets the CommercialID so the telemetry data reaches your Log Analytics workspace |
| Configure telemetry opt-in change notifications=Enabled, "Disable telemetry change notifications" | DisableTelemetryOptInChangeNotification=1 | Optional, prevents the notification to the user when the telemetry level is changed |
| Configure telemetry opt-in setting user interface=Enabled, "Disable telemetry opt-in Settings" | DisableTelemetryOptInSettingsUx=1 | Optional, prevents the user from changing the telemetry settings |
| Allow WUfB Cloud Processing=Enabled | AllowWUfBCloudProcessing=8 | Allows diagnostic data to be processed by WUfB Cloud |
Intune Method
To configure your devices using Intune, we first need to create a configuration profile containing the required MDM settings, and assign it to the devices you want to use with Update Compliance. Following this, deploy the configuration script as a Win32 app. The Docs page on this is pretty good so I'll link it here rather than type out the same steps: Configuring Microsoft Endpoint Manager devices for Update Compliance - Windows Deployment | Microsoft Docs
Speeding it up a little
It'll take about 72 hours for you to start to see some data coming through. The data comes from something called Census in Windows 10. This runs daily however static data such as device name, OS etc are only sent weekly. If you used the configuration script, it should have automatically run a full census. If you're using another method, you can force a full census by setting a registry key: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Census and add a DWORD named FullSync, with value set to 1. Run %systemroot%\system32\devicecensus.exe with administrative privileges, then change your FullSync registry setting to 0.
What it looks like with data in it
Returning to the Solution summary page, you should now see a bit of data has come in. I've taken this set of screenshots from a live environment rather than my lab so you can see what it looks like with a decent amount of data.
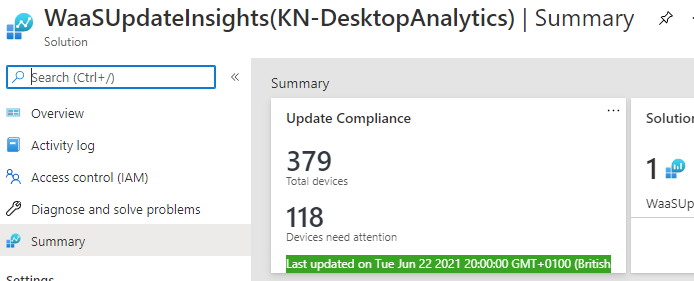
You can pin this to your Azure dashboard if you want, by clicking the pin button at the top right. Clicking on to the summary box will open the overview screen which should show you how many of your devices are up to date (or not). In my example I've caught it after Patch Tuesday but before the delay period for most devices has run out, so a lot showing as out of date.
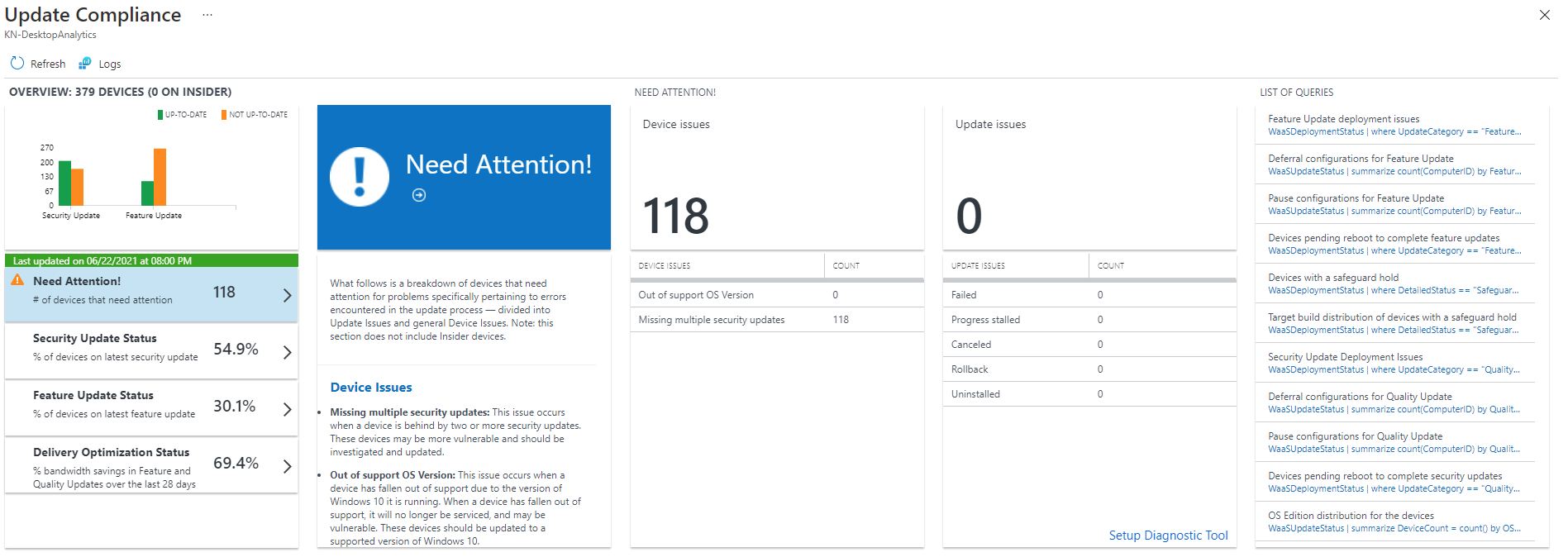
You can click on various items, such as the left hand panel, to bring up a set of graphs and charts:
- Need Attention - List of device issues (e.g. out of support, missing updates), along with update issues (e.g. failed, stalled, cancelled etc)
- Security Update Status - Chart showing OS version, device count up to date, and device count not up to date, along with the latest and previous security update deployment status.
- Feature Update Status - Chart showing OS version and feature deployment status
- Delivery Optimization Status - Charts showing how many devices are configured for delivery optimization, and the content distribution (peer vs HTTP).
In other areas, clicking on various items will bring up a query window and show you both the query it's running and the results.
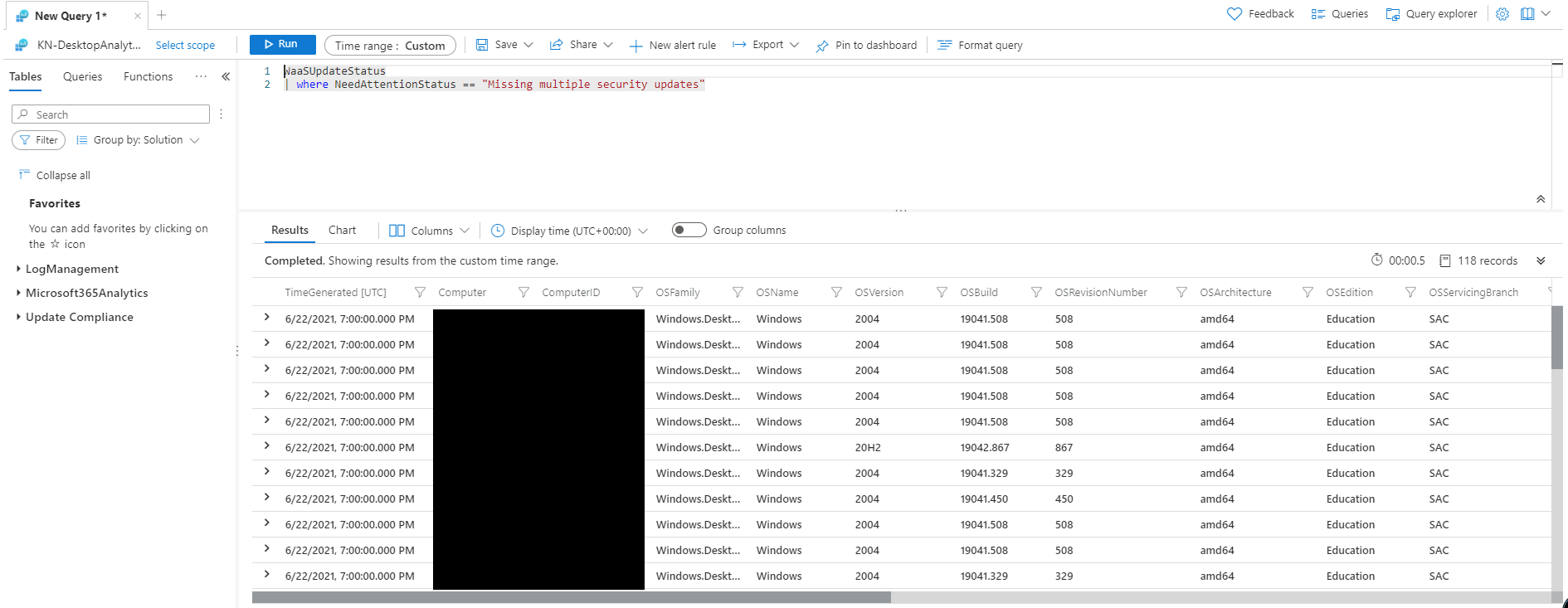
Clicking on some of the items will take you to a query window and show you the results in a table. This one's showing me which PCs are missing multiple security updates. While dropping back to the query view isn't as nice an interface as we had with WSUS, we can at least see the data (and if we wanted to look into the table data structure, we could write our own queries). The benefit of this data being stored in Log Analytics is that if we wanted we could write a custom workbook within Intune Reports to show the data we are really interested in.
New version?
Microsoft are working on an updated version of Update Compliance which looks like it will be vastly improved. I can't say much about this at the moment but hopefully there will be a public preview coming later in the year.
Further Reading
- Windows Update for Business (Windows 10) - Windows Deployment | Microsoft Docs
- Configure Windows Update for Business via Group Policy (Windows 10) - Windows Deployment | Microsoft Docs
- Learn about using Windows Update for Business in Microsoft Intune - Azure | Microsoft Docs
- Manage Windows as a Service - Configuration Manager | Microsoft Docs
- Get started with Update Compliance - Windows Deployment | Microsoft Docs
- Update Compliance Configuration Script - Windows Deployment | Microsoft Docs
- Configuring Microsoft Endpoint Manager devices for Update Compliance - Windows Deployment | Microsoft Docs
In this post
- Introduction
- Configuring Policies
- Monitoring Update Compliance
- Speeding it up a little
- What it looks like with data in it
- New version?
- Further Reading
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.