Azure: Conditional Access and MFA

Multi-factor authentication is a must in this day and age, with phishing techniques becoming more and more sophisticated and more difficult to detect/block. Azure MFA can be used to secure your Office 365 workload (and, if you're using it as the authentication method for other services, they can be secured too).
MFA is available in all of the levels of Azure AD licensing however it's most powerful when combined with Conditional Access, which requires Azure AD Premium P1 or P2. In this post I'm going to run through a few of the different rules I've set up on various tenancies.
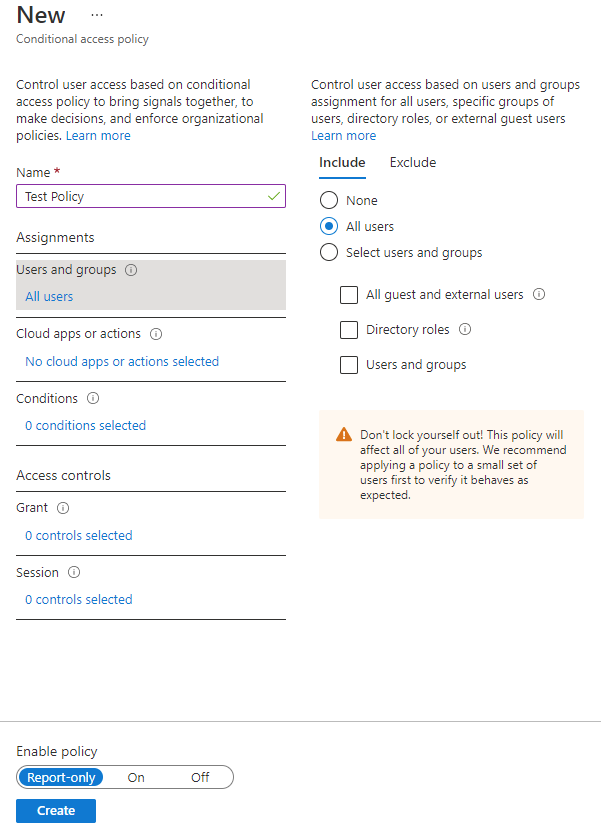
Conditional Access configuration can be found through Azure AD > Security > Conditional Access in the Azure portal. When you click New policy you should see something similar to the below. The settings I've detailed later in this post relate to the sections on this screen. When creating your policy you can set it to Report Only, On or Off. Report Only is useful when you first create the policy if you want to see where it would have been applied, but without it actually applying, to monitor any impact on users or where you may have misconfigured and would have ended up blocking sign ins.
Where you are using a policy to grant access, you can configure various requirements and can chose whether the user has to satisfy all of them or just one of them:
- Require MFA
- Require device to be marked as compliant - i.e. the device is Azure AD registered, or joined, and is in a compliant state
- Require hybrid Azure AD joined device
- Require approved client app
- Require app protection policy
Restrict MFA sign up
It's crucial that you restrict the MFA sign-up process to trusted locations only. If an account has been compromised and is also set to require MFA, for example "Require MFA for all sign-in attempts from outside the UK", but the user hasn't set up MFA yet then the first thing an attacker is going to see when signing in from another country is the MFA setup screen, where they will set up their own authenticator app on the compromised account.
- Assignments > All users
- Cloud apps or actions > User actions > Register security information
- Conditions > Locations > Include Any, Exclude trusted locations (or populate the list yourself with your on-premises public IP address)
- Conditions > Client apps > Browser and Mobile apps and desktop clients
- Access controls > Block access
Bypassing MFA for on-premise logons
Usually you'll want to skip MFA for users logging on when they are physically on site. This can be achieved through the MFA Service Settings page (which is not part of the Azure AD portal), enter your on-premise public IP address range(s) into the trusted IP box. You can also configure the verification modes available to users on this page, and configure whether users are allowed to "remember devices" to extend the lifetime of the login.
Configure MFA based on country
If you're not a global organisation you might want to apply different settings to login attempts from other countries. This can be particularly useful where you haven't enforced MFA yet but want some level of protection from compromised account logins, which in my experience don't originate in the UK. It's worth noting that this only applies to IPv4 addresses, IPv6 do not have geo location in Azure.
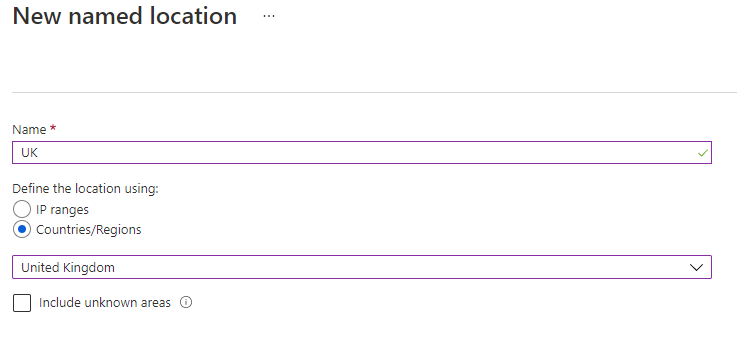
First of all you will need to create a named location. Go to Azure AD > Security > Conditional Access > Named locations and add an entry for your country. Define the location using Countries/Regions and select the country, or countries, you want to include.
You can now go back to Policies and create your Conditional Access policy as below:
- Users and groups > All users (or target a specific group)
- Cloud apps or actions> All cloud apps
- Conditions > Locations > Any location (Included), Selected locations (Excluded) - here select your country location
- Conditions > Client apps > Select them all
- Access controls > Grant > Require MFA
Configure for a specific app
You can configure a policy for a specific app. In this case I used this in conjunction with the location policy above, so that users were required to go through MFA if they were outside the UK, but also when accessing specific applications regardless of their physical location, unless they are physically on the main physical site.
- Users and groups > All users (or target a specific group)
- Cloud apps or actions > Include selected cloud apps (find your apps in the list)
- Conditions > Locations > Any location (Included), Select locations (Excluded), here I've selected the on-premise location entry although this can be omitted if you want to enforce it everywhere.
- Conditions > Client apps > Select them all
- Access controls > Grant > Require MFA
Service accounts
We use some service accounts for things such as Azure AD Connect and some scheduled PowerShell scripts which run on-premise. These are Azure AD/Office 365 cloud accounts with the required privileges for the workload they're running. We don't want these accounts to be able to log in from anywhere but our on-premise network so can create a conditional access rule to block external access.
- Assignments > Specific users included (select the service accounts)
- Cloud apps or actions > All cloud apps included
- Conditions > Locations > Any location (included), on-premise public IP address (excluded)
- Access controls > Block access
Blocking legacy authentication
Finally a policy to block legacy authentication. Prior to doing this you'll need to make sure modern authentication is enabled in your tenancy and that users are not using legacy apps.
- Users and groups > All users
- Conditions > Client apps > Select both the Legacy authentication clients
- Grant > Block access
Further Reading
In this post
- Introduction
- Restrict MFA sign up
- Bypassing MFA for on-premise logons
- Configure MFA based on country
- Configure for a specific app
- Service accounts
- Blocking legacy authentication
- Further Reading
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.