CM: Enabling BitLocker

Config Mgr comes with a Bitlocker Management section (under Endpoint Protection), however as far as I can tell this just allows you to set the Bitlocker policy but not force drives to be encrypted - at least I couldn't get it to do anything on devices it claimed were compliant.
I've got an OS deployment task sequence which installs Windows, and has a few BitLocker steps - however I forgot to set a variable telling it to use the TPM chips without additional PIN/password/keys for Bitlocker - so my computers built without Bitlocker being enabled.
Not wanting to go through the build process again for all these devices, I decided to push it out to existing devices through Config Mgr.
First you will need a device collection containing all devices that have TPM chips. Create a new device collection, I've called mine "TPM Devices", and add a Query membership rule. Click on Edit Query Statement -> Show Query Language, and paste in the following:
select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,
SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System
inner join SMS_G_System_TPM on SMS_G_System_TPM.ResourceId = SMS_R_System.ResourceId
where SMS_G_System_TPM.IsEnabled_InitialValue > 0
This will return any device where the TPM chip is enabled.
You can check if a device has a TPM chip (and if it's enabled) by running Get-TPM in PowerShell. I found on older devices where I had just enabled TPM in the BIOS that they needed to boot up to Windows and have a couple of reboots before TpmEnabled changed from False to True, and some needed to have Initialize-TPM run in PowerShell (followed by reboot) before they'd show up - I use the following script running through Config Mgr's Script section (see here for an example of the Scripts section).
if ((Get-Tpm).TpmEnabled -eq $false) {
Initialize-TPM
shutdown /r /f /t 5
}
Now go to Software Library\Operating Systems\Task Sequences and create a new task sequence. Select a custom task sequence, give it a name (e.g. Enable bitlocker), and complete the wizard. Don't select a boot image.
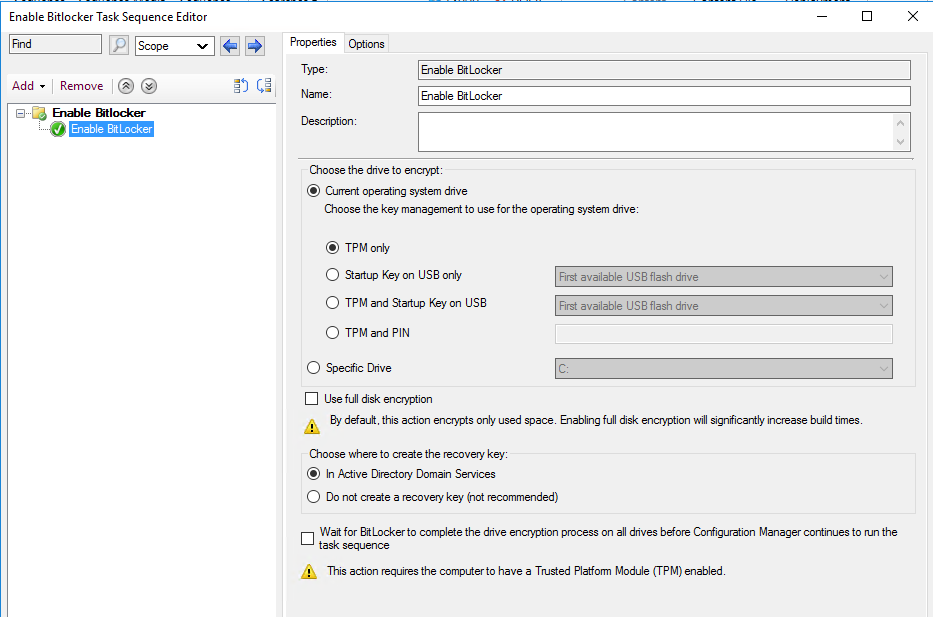
Edit your new task sequence, go to Add -> New Group, then Add -> Disks -> Enable Bitlocker. You can probably leave the settings at their defaults (I have on my system).
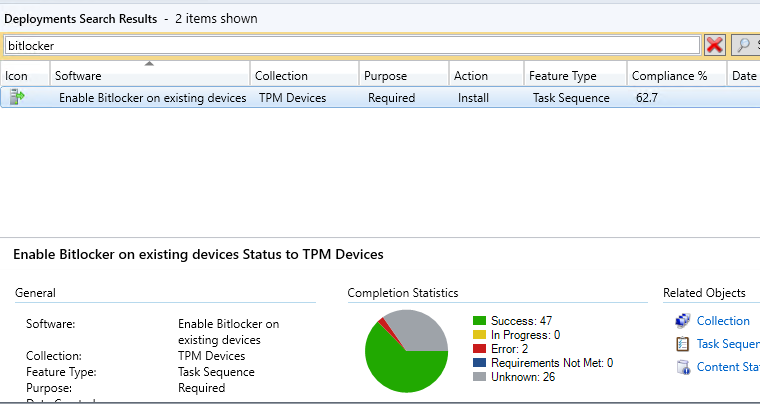
Now we need to deploy our task sequence. Right click on the task sequence and select Deploy. Run through the usual deployment wizard, selecting your TPM Devices collection, set the Purpose to "Required" and set the schedule to "ASAP" (or whatever your requirements are). I tend to untick "Show Task Sequence progress" on the User Experience page, as I don't want anything popping up in the computers are in use when the task runs.
Finish the wizard and you should now have a deployment, all you have to do now is wait!
You can monitor the progress in the usual manner - Monitoring\Deployments and search for your task sequence name.