Silently enable BitLocker with PIN during Autopilot
BitLocker is Microsoft's disk encryption system and the only supported silent configuration involves the TPM only. There are other options such as also requiring a start-up PIN or a physical key (USB drive containing the key), or both - whether you think you need the extra security at the risk of PIN re-use/being written down is an exercise left to the reader. However I wanted to find a way to enable BitLocker with a PIN required at start-up on a device deployed through Autopilot, without the user having to do anything to enable the protection. While there are configuration profiles which can configure BitLocker to require a PIN and to require the device encryption, this won't actually prompt the user to encrypt the device if you're requiring additional authentication to unlock the drive. Looking forward it would be nice to see this supported - as a step in the OOBE process or on the Enrolment Status Page, asking the user for a PIN and enabling the encryption. But for now, we have to come up with our own solutions - my solution involves a PowerShell script which enables the encryption using the device serial as the key. The user can then be given instructions to change this once logged on.
Configuration Profiles
For this solution to work, there are a few required configuration profile items we need to push to the devices. Create two configuration profiles as below and assign them to the devices you wish to encrypt. To cover all future Autopilot devices you may wish to assign to All Devices, possibly with a filter targeting the enrollmentProfileName, or to a dynamic device group.
Besides this make sure the device is protected with Secure Boot and a BIOS password.
Endpoint Protection profile
This profile can be created through selecting Templates > Endpoint Protection in Intune. Configure the following settings:
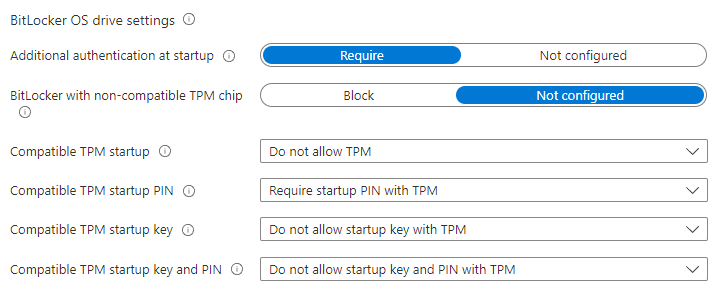
BitLocker OS drive settings
- Additional authentication at startup: Require
- Compatible TPM startup: Do not allow TPM
- Compatible TPM startup PIN: Require startup PIN with TPM
- Compatible TPM startup key: Do not allow startup key with TPM
- Compatible TPM startup key and PIN: Do not allow startup key and PIN with TPM
Other settings may be configured here such as the minimum PIN length and the encryption type, but are not strictly required.
Settings Catalog profile
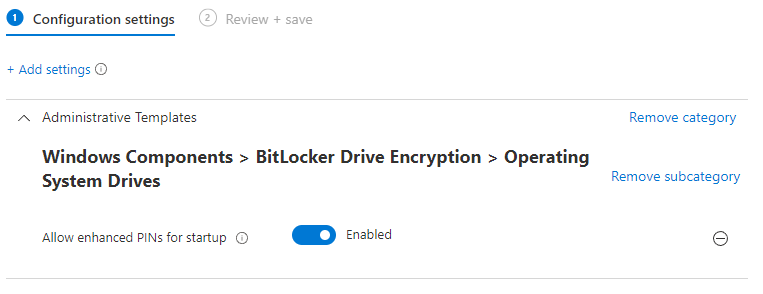
A further setting is required, which is not available in the Endpoint Protection profile. This enabled enhanced PINs which is required if we want to use letters in the PIN - as they are usually part of the serial number. This profile can be created through selecting Settings Catalog in Intune. Find the following item and add it to the profile, and set to Enabled:
Windows Components > BitLocker Drive Encryption > Operating System Drives - Allow enhanced PINs for Startup
Finally, for this to work with some touch devices, a setting is required to force Windows to allow BitLocker to require unlock methods which need a pre-boot keyboard. If the devices do not have a physical keyboard attached which functions in the pre-boot environment, the user will not be able to enter the PIN.
Windows Components > BitLocker Drive Encryption > Operating System Drives - Enable use of BitLocker authentication requiring preboot keyboard input on slates
Encryption Script
The script I have written will query the device for the BitLocker status of the OperatingSystem volume. If it is currently reporting FullyDecrypted, get the device serial number in upper case, create a recovery password key protector, enable BitLocker with the serial as the PIN, and then back up the recovery password to Azure AD. Once this has run, a restart is required to fully enable BitLocker - if this is running during Autopilot there will usually be a restart at some point after it has run.
$OSVolume = Get-BitlockerVolume | Where {$_.VolumeType -eq "OperatingSystem"}
if ($OSVolume.VolumeStatus -eq "FullyDecrypted") {
$DeviceSerial = ((Get-WmiObject win32_bios).Serialnumber).ToUpper()
$DevicePIN = ConvertTo-SecureString $DeviceSerial -AsPlainText -Force
Add-BitlockerKeyProtector -MountPoint $OSVolume.MountPoint -RecoveryPasswordProtector
Enable-BitLocker -MountPoint $OSVolume.MountPoint -Pin $DevicePIN -TPMandPinProtector
$RecoveryKeyID = ((Get-BitlockerVolume).KeyProtector | Where {$_.KeyProtectorType -eq "RecoveryPassword"}).KeyProtectorId
BackupToAAD-BitlockerKeyProtector -MountPoint $OSVolume.MountPoint -KeyProtectorId $RecoveryKeyID
}
Save the script - or download it from the GitHub repository - and go to Intune portal > Devices > Scripts and create a new script with the following settings:
- Script file: (Upload the script)
- Run this script using the logged on credentials: No
- Enforce script signature check: No
- Run script in 64 bit PowerShell Host: No
Finally assign the script to the devices you want to protect - as with the configuration profiles, a filter or group which will automatically include future Autopilot devices is a good choice.
What next?
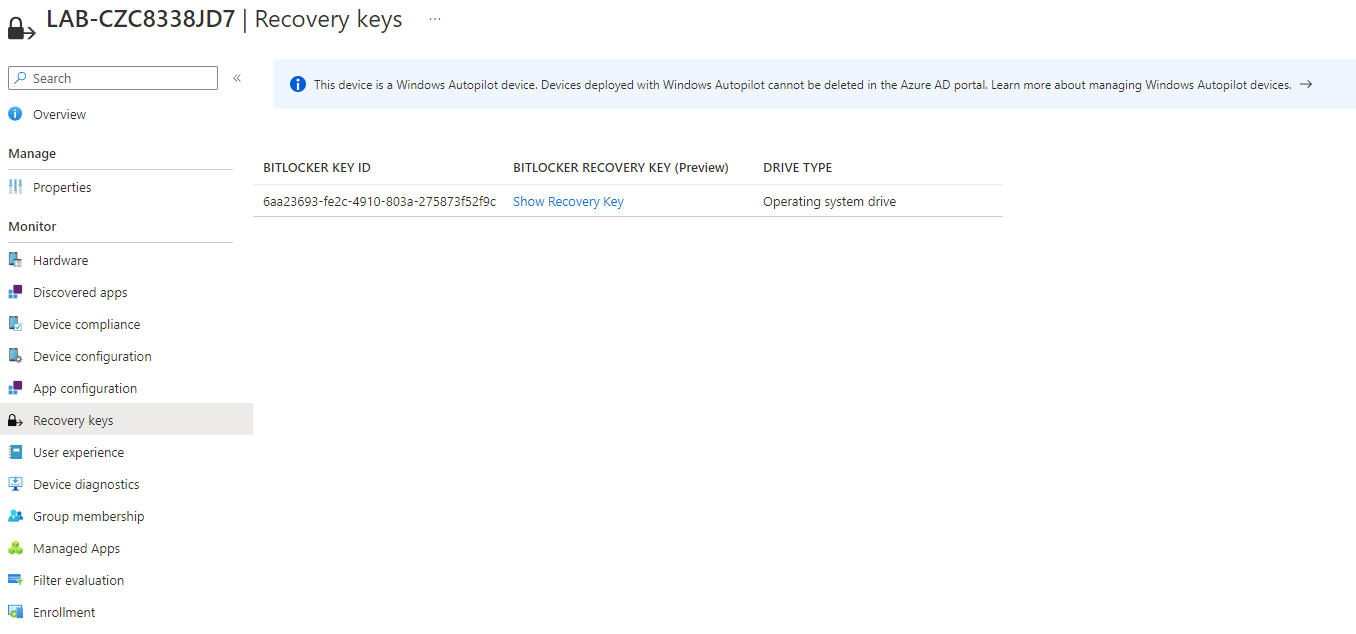
Your devices should now run this script silently during Autopilot, and the device will require its serial number in upper case as the unlock PIN. The user can then change the PIN themselves through Explorer - right click on the OS Disk volume, and change PIN. Administrator privileges are not usually required unless the PIN has been forgotten and needs resetting. Should the user lose the PIN and be locked out of the device, the recovery password will be available in Intune by going to the device's detail screen and selecting Recovery Keys.
If it doesn't seem to be working, run the script manually in a PowerShell window and the error messages should indicate where the issue is. This is usually where the BitLocker policy settings (GPO or CSP) are conflicting with what we are trying to do.
Further Reading
In this post
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.

