Azure AD Terms of Use
Azure AD's terms of use feature allows us to present information to users which they need to accept/acknowledge before being permitted access to a service. The feature supports multiple languages and essentially you upload a PDF for each supported language for your Terms of Use policy. You can create multiple policies if needed. Possible use cases for this include for users enrolling their personal Windows device through Access work or school, where they can be presented with some rules before their device will give them access, or even when accessing specific services such as Microsoft Forms in the browser, if you wanted to display some usage guidance for using Forms in your organisation.
Before I get started, I need to point out that there is also a feature called Terms and conditions in Intune, available through the Tenant Administration section. This is a completely separate feature to Azure AD Terms of Use, and has a limited feature set. This post covers the Azure AD Terms of Use only.
There are two sections to this feature - the first creates the terms of use policy, which contains the actual terms documents and whether you want users to have to consent once, or once on every device, or perhaps you may want them to have to re-consent after a specific period of time. The other side to this is a Conditional Access rule. The terms of use policy appears in Conditional Access as a grant requirement - so where you'd traditionally expect to see grant requirements such as Hybrid joined, or compliant device, or MFA, you'll now also see your Terms of Use policies.
Configure Terms of Use
Terms of Use can be found through Intune Portal > Endpoint security > Conditional Access > Terms of use. Select New terms to create your new Terms of Use policy.
When creating your policy, the name is only displayed internally in Conditional Access, and isn't visible to the end user. The name displayed to the end user is the Display name field, which can be localised. Make as many policies as you require, you can tailor each terms policy to the service it protects.
You will need to prepare some PDF files, one per language that you wish to support, containing the actual terms of use content, these can then be uploaded, their language identified, along with their display name.
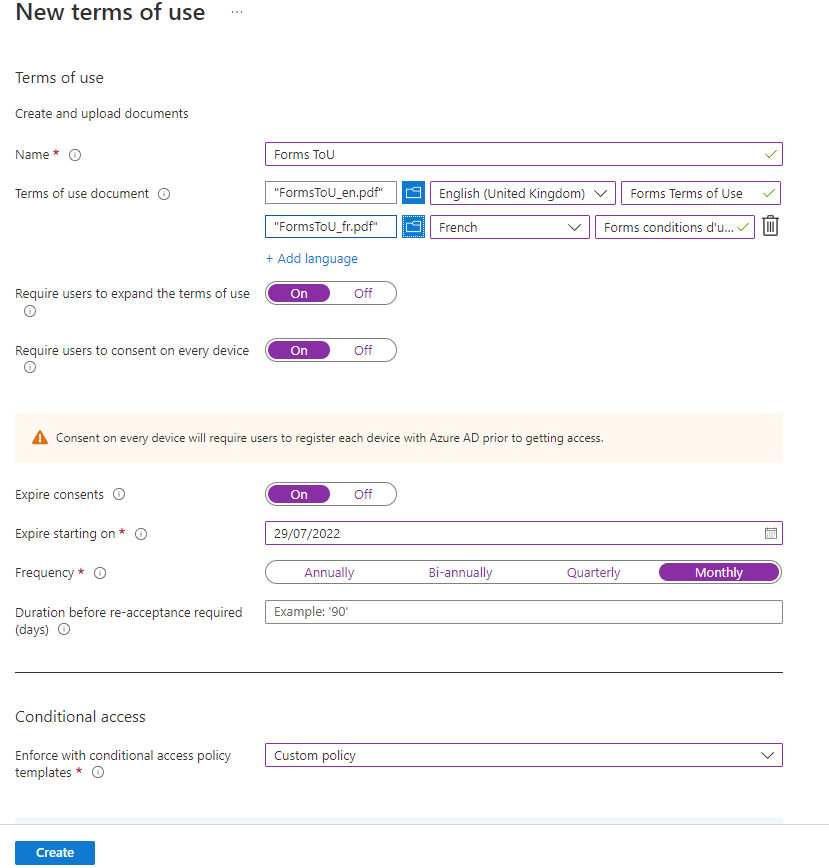
Most of these settings are self explanatory but a couple which need some further explanation:
- Require users to consent on every device - this will require the device to be registered with Azure AD before the user can consent. Typically this will mean the user has to use a managed browser, such as Edge, and be signed in to the browser in order to continue.
- Expire consents on/Frequency - you can set a specific, static date when users will be required to re-consent, and you can require re-consent on a schedule - annually, bi-annually, quaterly or monthly.
- Duration before re-acceptance required - you can set the frequency that users must re-consent. Similar to the above settings except you can set a specific number of days, e.g. 90 for "every 90 days", rather than picking a start date and frequency.
- Enforce with conditional access policy templates - if you select Custom policy then you will be taken to the New Conditional Access policy flow once this has been created, if you select Create later you won't be.
Configure Conditional Access rule
The next step is to create a Conditional Access rule to enforce your terms of use. If you selected Custom policy as the template in the previous step, you should now be sat at the Conditional Access screen.
Example 1: Microsoft Forms terms of use
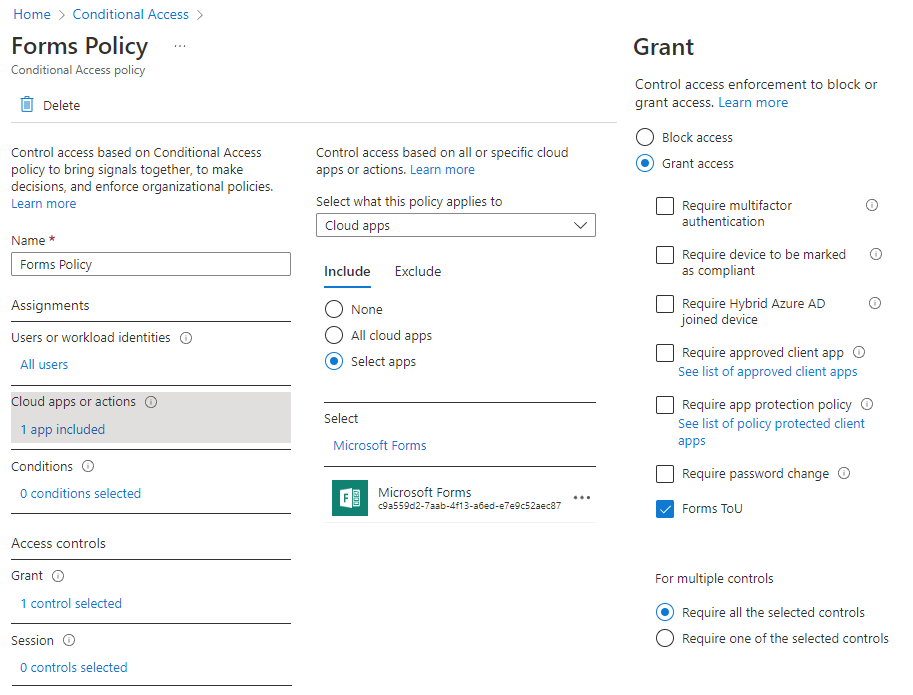
In this example I want to present users with some usage guidance before they can access Forms. I've set up a very basic Conditional Access policy, opting to apply this to all users, for the selected Cloud App (Microsoft Forms), and Grant requirement is Forms ToU.
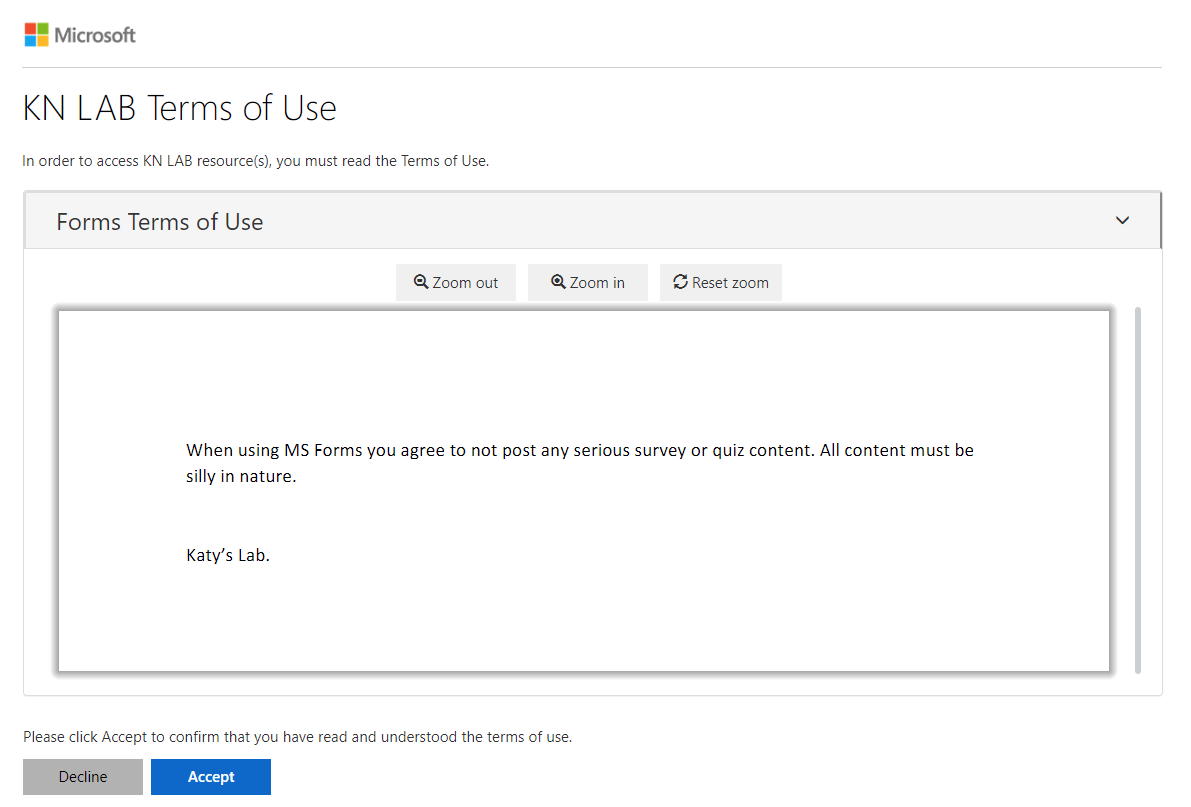
End User experience
When the user goes to Microsoft Forms and signs in, they will be redirected to accept the Terms of Use document. The language will be automatically detected based on their browser settings.
Example 2: Windows device enrolment into Intune
This example is much more complex and involves showing terms of use to people bringing their own Windows device and wanting to access corporate data using the Access work or school feature - either through Windows settings, or through signing in to an app and leaving the Manage this device box ticked. I've targeted this to all users except my admin account, for the Microsoft Intune cloud app. There is also a cloud app called Microsoft Intune Enrolment - when testing this one didn't seem to work, so I've gone with just Microsoft Intune. The grant requirement here is the Intune Terms of Use policy that I have defined earlier.
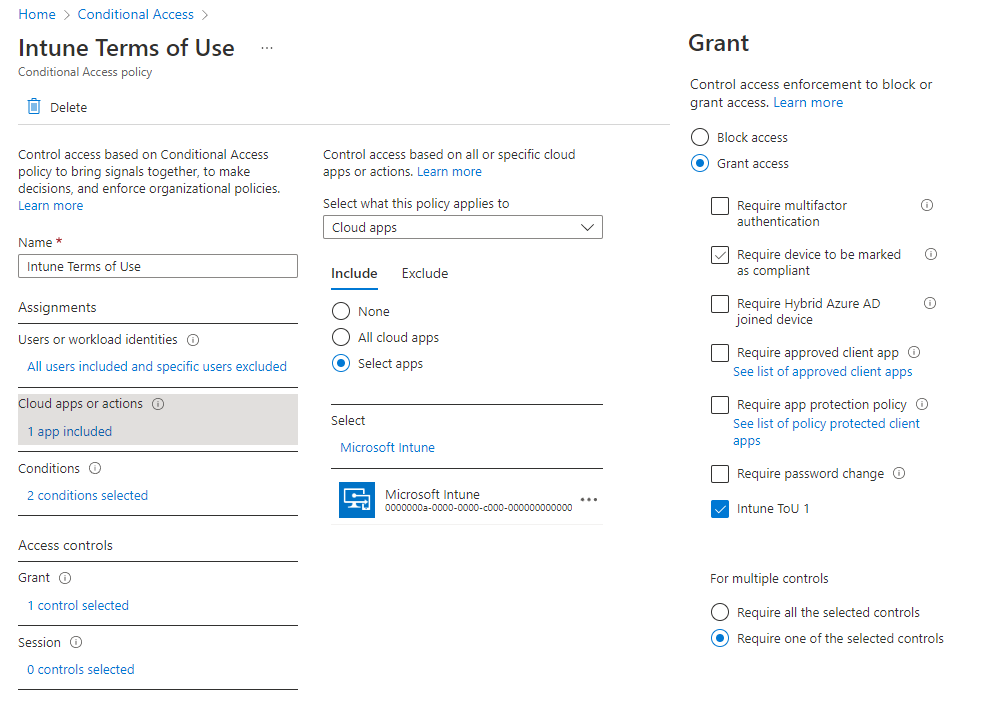
You will want to further restrict this to Windows devices only and include a filter for devices, to exclude corporate owned devices (device.deviceOwnership -eq "Company"), and perhaps alter the grant to require compliant devices or the Terms of Use. Much testing needed before this is released in the wild!
End User experience
When I tested this on a Windows 10 VM, simulating a BYOD device as it was not joined to a domain or managed in any way, I went through Settings, Access work or school, and selected Sign in. I followed through the steps to sign in and eventually this notification appeared near the system tray:
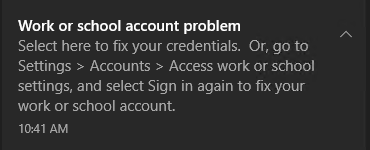
Clicking this will take you back to the Access work or school settings page, which should then pop up the Terms of Use for the user to accept.
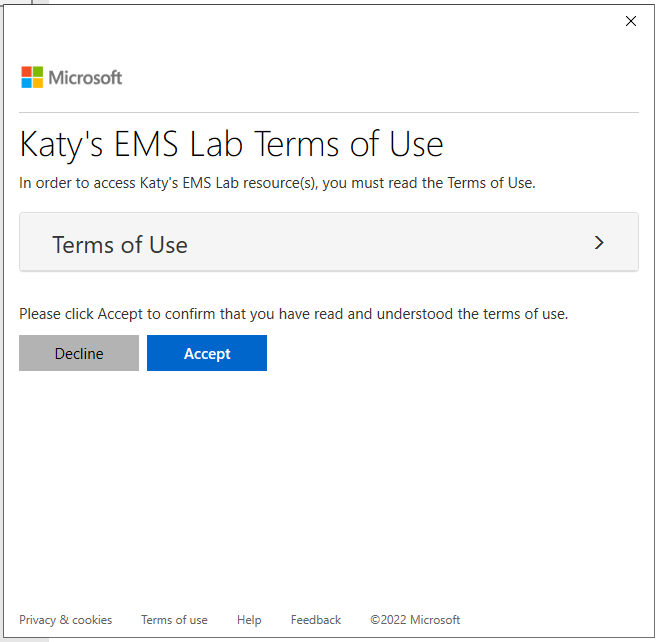
The user experience for this isn't the best but with some tweaking this could work, but it's just one example of a more complex use case for terms of use and conditional access.
Further Reading
In this post
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.

