Restricting printing to specific devices or device types
Device Control Printer Restriction has been around for a while and can be configured using a couple of CSP entries to block the use of "non-corporate printers", and a list of USB hardware IDs can be specified to be allowed through the block. This has been a good solution for locking down printing on devices which leave the office, however the definition of "corporate printers" does not include Universal Print. Luckily there is a new version of this policy, confusingly it's got the same name but uses Defender's device restriction mechanism. Using this new method we can define groups of devices and create a list of rules to apply.
This requires Microsoft Defender for Endpoint Plan 1 or Plan 2.
Most of the setup of this involves creating XML files which have IDs - these are not specific IDs and you can just create a new GUID for each, for example by running New-GUID in PowerShell.
Printer Groups
Printer Groups define the device you are trying to restrict or allow. This can be as simple as "any printer", or as specific as "only this specific Vendor ID/Product ID". See the XML later in this post for how these fit together.
- Group ID: A GUID for this group
- Name: The group name displays on toast notifications and in reporting
- Type: The group type, e.g. device/network/vpn
- MatchType: if there are multiple descriptors, the method of matching them
- MatchAll
- MatchAny
- MatchExcludeAll
- MatchExcludeAny
- DescriptorIdList: A list of various attributes to determine the printer. Full details available on Microsoft Learn, briefly:
- PrimaryId: RemovableMediaDevices/CdRomDevices/WpdDevices/PrinterDevices
- FriendlyNameId: The name as shown in Device Manager
- VID_PID: The device VID and PID as shown in Device Manager
- PrinterConnectionId: The type of printer connection
- USB
- Corporate: Shared printer on the on-premises AD domain
- Network
- Universal: Universal Print devices
- File: Print to file, e.g. PDF printer or XPF printer. This can be combined with FriendlyNameId to restrict specific printers
Access policy rule
Access policy rules define which combination of factors will be allowed or denied, referencing one or multiple printer groups, and even non-printer things such as the network or whether a VPN is connected - this can be used for things such as only allowing USB printers when on the corporate LAN. Examples of the XML files can be found further down this page.
The full details on the access policy rules are available on Microsoft Learn however I'll briefly go through the more useful ones here.
- PolicyRule ID: A GUID for this rule
- Name: The policy name displays on the toast notification and in any reporting
- IncludedIdList: A list of Printer Group IDs to include in this rule
- ExcludedIdList: A list of Printer Group IDs to exclude from this rule
- Entry: An individual restriction. Each policy rule can have multiple entries.
- Entry ID: A GUID for this restriction entry.
- Type: Defines what the action is for the groups in this policy rule.
- Allow: Print jobs will be allowed
- Deny: Print jobs will be blocked
- AuditAllowed: Audit actions to take when the print job is allowed
- AuditDenied: Audit actions to take when the print job is blocked
- Options: Varies depending on the Type. See Microsoft Learn for full details.
- AccessMask: No idea. This is set to 64 in all the Microsoft examples however their documentation just states that Access Mask "defines the access".
- Parameters: Used for network/VPN rule conditions.
Configuring the XML
Any Printer Group
This file defines which printers we want to target in our policy. In this case it is any printer.
<Group Id="{c13864b5-1b90-4e45-ba59-9494717065b5}" Type="Device">
<!-- ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bc13864b5-1b90-4e45-ba59-9494717065b5%7d/GroupData -->
<Name>Any Printer</Name>
<MatchType>MatchAny</MatchType>
<DescriptorIdList>
<PrimaryId>PrinterDevices</PrimaryId>
</DescriptorIdList>
</Group>
Universal Print Group
This file defines all Universal Print devices.
<Group Id="{f4c4e4d8-e7ad-4829-ac16-190a70c401ce}" Type="Device">
<!-- ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bf4c4e4d8-e7ad-4829-ac16-190a70c401ce%7d/GroupData -->
<Name>Universal Print</Name>
<MatchType>MatchAny</MatchType>
<DescriptorIdList>
<PrinterConnectionId>Universal</PrinterConnectionId>
</DescriptorIdList>
</Group>
Policy Rule: Allow Universal Print
This policy rule sets out an Allow rule for anything matching the Universal Print Group.
<PolicyRule Id="{f312f13e-89ee-4061-ab9d-3e25b18decdd}">
<!-- ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bf312f13e-89ee-4061-ab9d-3e25b18decdd%7d/RuleData -->
<Name>Allow Universal Print</Name>
<IncludedIdList>
<GroupId>{f4c4e4d8-e7ad-4829-ac16-190a70c401ce}</GroupId>
</IncludedIdList>
<ExcludedIdList />
<Entry Id="{580c1ecd-65ef-4bab-8c4b-3ba32b98f1a0}">
<Type>Allow</Type>
<Options>0</Options>
<AccessMask>64</AccessMask>
</Entry>
</PolicyRule>
Policy Rule: Default deny all
This policy rule sets out a Deny rule for everything matching the Any Printer group, and excludes the Universal Print group. If a user's print job is blocked by this rule, an event is raised and a toast notification is shown to the user.
<PolicyRule Id="{c1dac13a-eb0a-41c4-91a9-749451c33e23}">
<!-- ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bc1dac13a-eb0a-41c4-91a9-749451c33e23%7d/RuleData -->
<Name>Default Deny</Name>
<IncludedIdList>
<GroupId>{c13864b5-1b90-4e45-ba59-9494717065b5}</GroupId>
</IncludedIdList>
<ExcludedIdList>
<!-- exclude Universal print group -->
<GroupId>{f4c4e4d8-e7ad-4829-ac16-190a70c401ce}</GroupId>
</ExcludedIdList>
<Entry Id="{2d946a29-579d-4a65-9020-2d9fd6b9cf8b}">
<Type>Deny</Type>
<Options>0</Options>
<AccessMask>64</AccessMask>
</Entry>
<Entry Id="{48fe1c20-83ef-4163-aa99-882f49f3ec1d}">
<Type>AuditDenied</Type>
<Options>3</Options>
<AccessMask>64</AccessMask>
</Entry>
</PolicyRule>
Intune Configuration
Unfortunately there are no built in settings to configure this in Intune, so we have to create a custom device configuration profile.
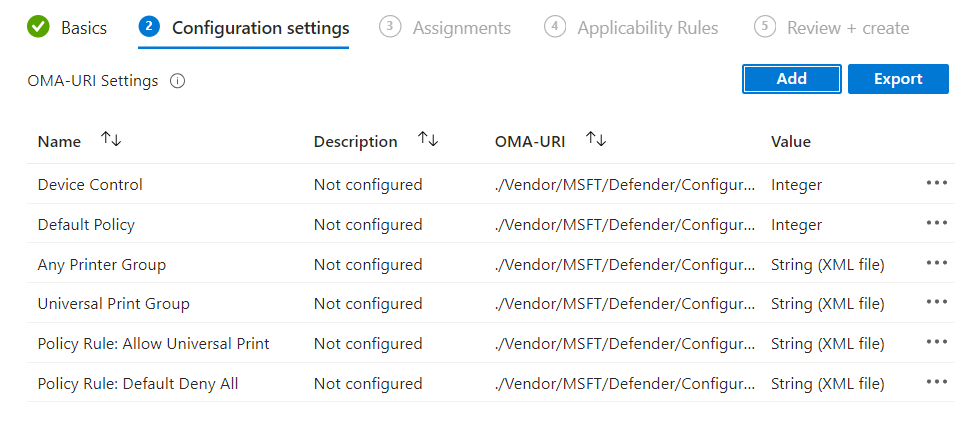
- Create a new device configuration profile, select the type as Templates and then Custom
- Add an entry to turn on (or off) device control:
- Name: Enable Device Control
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControlEnabled
- Type: Integer
- Value: 1 (Enabled) or 0 (Disabled)
- Add an entry to set the default policy:
- Name: Default Policy
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DefaultEnforcement
- Type: Integer
- Value: 1 (Allow) or 2 (Deny)
- Add one entry for each of the group files:
- Name: Any Printer group
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bc13864b5-1b90-4e45-ba59-9494717065b5%7d/GroupData (Note the GUID here is the Group ID GUID defined in the XML file)
- Type: String (XML file)
- Value: (Select the Any Printer XML file created earlier)
- Add the second group file:
- Name: Universal Print group
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bf4c4e4d8-e7ad-4829-ac16-190a70c401ce%7d/GroupData (Note the GUID here is the Group ID GUID defined in the XML file)
- Type: String (XML file)
- Value: (Select the Universal Print XML file created earlier)
- Add one entry for each of the policy rule files:
- Name: Policy Rule: Allow Universal Print
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bf312f13e-89ee-4061-ab9d-3e25b18decdd%7d/RuleData (Again note the GUID is that of the PolicyRule ID)
- Type: String (XML file)
- Value: (Select the Allow UP XML file created earlier)
- Add the second policy rule file:
- Name: Policy Rule: Default deny all
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bc1dac13a-eb0a-41c4-91a9-749451c33e23%7d/RuleData (Again note the GUID is that of the PolicyRule ID)
- Type: String (XML file)
- Value: (Select the Default deny all XML file created earlier)
Assign the profile to user or device groups in the usual way and sync your devices. I don't think a restart is required.
End User Experience
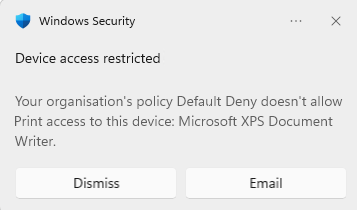
If the profile has been applied successfully, and the XML and other parts configured correctly, the user should now be unable to print except where defined by the rules set. If you have configured an AuditDeny entry to show the toast notification, then when the user tries to print and is blocked a toast notification will inform them of this. Otherwise the failure is silent to the user.
Troubleshooting
A log is kept of failed print jobs, this is in the Microsoft\Windows\PrintService application/service log in Event Viewer. Failed prints will log event 871, "The current print job was rejected due to Device Control Print Restrictions. Rejection Reason: Print blocked by Defender rule".
When the configuration is delivered to the device, the rules and groups are merged together and set into two registry settings:
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\Device Control\Policy Rules\Policy Rules
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\Device Control\Policy Groups\Policy Groups
Updates to these settings are shown in the Microsoft\Windows\Windows Defender application/service log - look for event ID 5007 which will show you the old and new value of the respective registry settings.
It also pays to be as simplistic as possible when writing policies - I found if I mixed a Universal Print group and a File (Print to PDF/XPS Writer) in a single Allow rule, by adding both Group IDs, it would not work, but if I split this out into two separate Allow rules, one for Universal Print and one for the PDF/XPS, then it did work.
There is a basic user interface for setting these within Intune which is in preview - using Endpoint Security Attack Surface Reduction - Device Control, sets of "reusable settings" can be combined into rules. You can read more about this on the Microsoft Learn site.
Further Reading
In this post
- Introduction
- Printer Groups
- Access policy rule
- Configuring the XML
- Intune Configuration
- End User Experience
- Troubleshooting
- Further Reading
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.

