Windows Autopatch
Windows Autopatch is a service which takes care of updates to Windows, Microsoft 365 Apps for enterprise, Microsoft Edge, and Microsoft Teams across your devices. It is marketed as taking the mundane tasks of managing updates away from IT staff, leaving them free to work on other things. Autopatch uses various policies and profiles through Intune to set the update configuration on the client devices, Windows Update for Business to deliver the updates, and reporting is also done through Intune (or the Update Compliance Log Analytics solution). Autopatch uses four rings to phase updates across your devices - test, first, fast and broad - where test gets the updates as soon as they become available, broad gets them with a 9 day delay, so that any issues are caught in the test or first rings and further deployment can be paused.
The four update rings used by Autopatch have a default device count - you can manually move devices from one ring into another, for example if the CEO's device has been put into the first ring, you can move it to broad.
| Ring | Device Count | Notes |
|---|---|---|
| Test | 0 | No devices are automatically placed into this ring, they must be added manually. The recommended device count varies depending on the total number of devices managed with Autopatch: 0-500 devices it's at least 1 device, 500-5000 at least 5 devices, and 5000+ at least 50 devices. |
| First | 1% | First production users to receive updates. There's a higher chance of update issues in this ring as not all scenarios (hardware, applications etc) have been covered in the test ring. |
| Fast | 9% | Second set of production users to receive updates. The idea here is that there will be enough devices to get sufficient data in order to determine if the update should be pushed out to the Broad ring or if it should be paused. |
| Broad | 90% | The final group of users to receive updates. |
Zero-day updates have an expedited release, so will go out to all devices as soon as possible - with 0 day deferral, 1 day deadline and 1 day grace period - and not follow the four ring configuration.
Pre-requisites
There are some licensing and technical pre-requisites for using Windows Autopatch:
Licensing Requirements:
- M365 E3/E5, or Windows Enterprise E3/E5
- Intune (included in M365 E3/E5)
- Azure AD Premium (P1 or P2) - included in M365 E3/E5
Technical Requirements:
- Windows 10 (1809 or later) or Windows 11 installed on your endpoint devices
- Hybrid Azure AD Joined, or Azure AD Joined devices
- Enrolled into Intune - either directly or via co-management
- Corporate-owned devices (personal owned/BYOD are not supported)
- Any update rings which target All users or All devices must either be removed, or changed to target a group.
For co-managed devices, there are some further requirements:
- Requires a currently supported Config Manager version
- Must be cloud-attached with the Windows Update, Device Configuration and Office Click-to-run apps workloads switched to Pilot Intune or Intune
Windows Autopatch can also be used on Windows 365 Enterprise Cloud PCs.
The full, detailed list of pre-requisites can be found on the Microsoft Docs: Autopatch Prerequisites
Enrolling
To start the enrollment process, open Intune Portal > Tenant administration > Windows Autopatch Tenant enrollment and tick the box. This will run the readiness tool which checks you have met the pre-requisites before enrolling your tenant. If this fails for any reason, it will show a Readiness status of Not ready, and you can then select View details to see what you've missed. Once you've fixed any issues, simply select Run checks to get the tool to run the checks again. There's more detail about the issues which the readiness tool may find on the Microsoft Docs: Fix issues found by the readiness tool

When any issues found by the readiness check have been resolved, you can go ahead and select Enroll. This will then ask for your consent to allow Microsoft certain access to your tenant - required for setting up Autopatch and also for the support team should there be issues which they need to resolve.
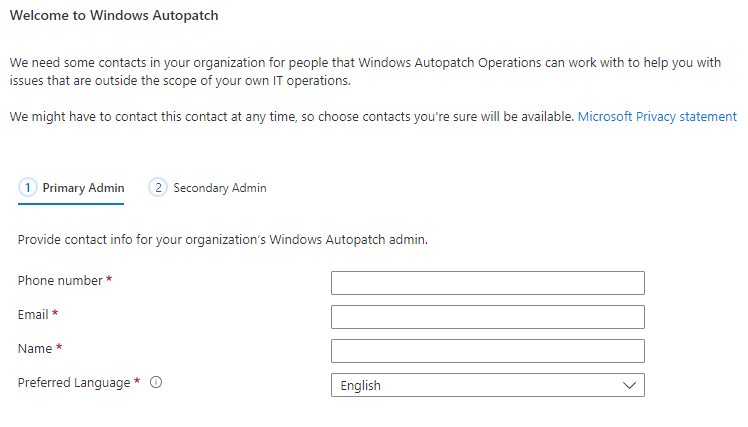
Once you've granted permission for the tenant access, you'll need to provide contact details for two administrators. These can't be the same person, and you have to provide both of them - even if you're just testing things. in a lab. When you've finished this step, Autopatch will set up the various accounts, groups, policies and profiles that it needs. At this point, your tenant has Autopatch enabled and ready to use - but there will not be any devices registered for Autopatch at this point.
Registering Devices
Now that your tenant is enroled in Autopatch, you will need to register some devices. The way devices are registered is fairly simple - put them in the Windows Autopatch Device Registration group. This is an Azure AD group, unfortunately changing this to a dynamic device group is not supported. Go to Intune Portal > Devices > Windows Autopatch Devices and you should find a link to your Windows Autopatch Device Registration group, selecting this will open the Azure AD group where you can add devices.
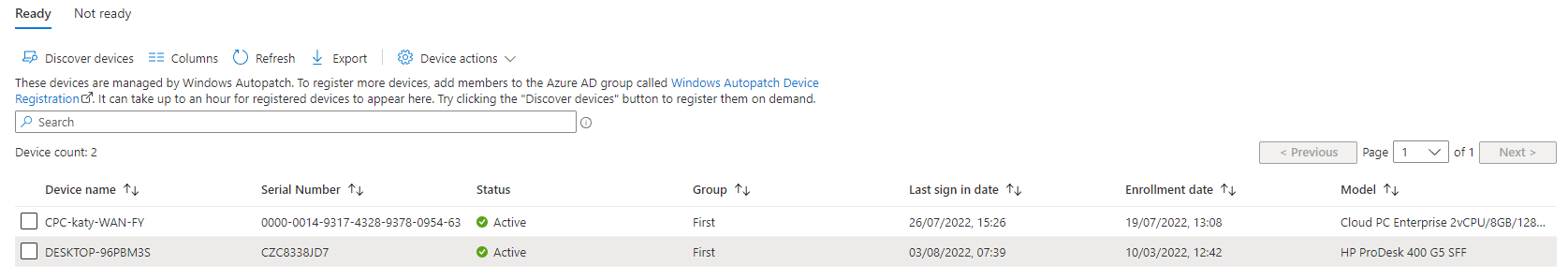
Once you've added your devices to the group, you can select Discover devices to have the Autopatch service check the group. It says it might take up to an hour, when I tried this it took a couple of minutes, although my test group only has 2 devices in it.
New devices registered into Autopatch will automatically be assigned to an update ring, based on the weighting mentioned earlier - 1% in first, 9% in fast, 90% in broad. You can manually change the ring for one or many devices by selecting the devices and then going to Device actions then Assign device group. This is useful if you have some devices you want to force to be in the broad ring, e.g. CEO laptop, or some test devices you want to move into the test ring.
All of the management of Autopatch is done through this blade of the Intune portal. It would be nice if there was some mention of Autopatch within the device's record page within Intune Devices, maybe that is something that will be coming in a future release.
What does it do in the backend?
So now that your tenant is enroled and your devices registered, what actually does Autopatch do? In the backend it creates various groups, policies and profiles to apply a managed update configuration. These are standard components of Intune such as update rings, feature update profiles and configuration profiles, so as far as the device is concerned it is just using Windows Update for Business. All Autopatch is doing here is managing the policy on Intune, making decisions in the background as to whether to pause update for the next ring, and offering support.
Autopatch creates 4 update rings named in the format Modern Workplace Update Policy [RingName]-[Windows Autopatch] with the following deferral settings:
| Ring | Feature Deferral | Quality Deferral | Deadline | Grace |
|---|---|---|---|---|
| Broad | 0 | 9 | 5 | 2 |
| Fast | 0 | 6 | 2 | 2 |
| First | 0 | 1 | 2 | 2 |
| Test | 0 | 0 | 0 | 0 |
It creates 5 feature update profiles, at time of writing these were set to the most recent Windows 10 release (except the Windows 11 policy):
- Modern Workplace DSS Policy [Broad]
- Modern Workplace DSS Policy [Fast]
- Modern Workplace DSS Policy [First]
- Modern Workplace DSS Policy [Test]
- Modern Workplace DSS Policy [Windows 11]
It creates 5 groups in Azure AD:
- Modern Workplace Devices-Windows Autopatch-Test
- Modern Workplace Devices-Windows Autopatch-First
- Modern Workplace Devices-Windows Autopatch-Fast
- Modern Workplace Devices-Windows Autopatch-Broad
- Windows Autopatch Device Registration
Autopatch creates 18 configuration profiles:
- Modern Workplace - Data Collection
- Modern Workplace - Edge Update ADMX Deployment
- Modern Workplace - Edge Update Channel Beta
- Modern Workplace - Edge Update Channel Stable
- Modern Workplace - Office ADMX Deployment
- Modern Workplace - Office Configuration v5
- Modern Workplace - Office Update Configuration [Broad]
- Modern Workplace - Office Update Configuration [Fast]
- Modern Workplace - Office Update Configuration [First]
- Modern Workplace - Office Update Configuration [Test]
- Modern Workplace - Set MDM to Win Over GPO
- Modern Workplace - Telemetry Settings for Windows 10
- Modern Workplace - Telemetry Settings for Windows 11
- Modern Workplace - Windows Update Detection Frequency
- Modern Workplace Update Policy [Broad]-[Windows Autopatch]
- Modern Workplace Update Policy [Fast]-[Windows Autopatch]
- Modern Workplace Update Policy [First]-[Windows Autopatch]
- Modern Workplace Update Policy [Test]-[Windows Autopatch]
You may be thinking that you can alter these settings as they are just standard Intune profiles - while it won't stop you from doing so, and doesn't appear to impact on the service actually working, changing the settings is not supported by Microsoft.
Reporting
Reporting for Windows Autopatch is done through a new Quality Updates report: Intune Portal > Reports > Autopatch Quality Updates. There is also the Windows Updates report - although this shows data about all devices, not just the Autopatch registered ones: Intune Portal > Reports > Windows updates (preview). For additional reporting you will need to look into the Update Compliance Log Analytics solution.
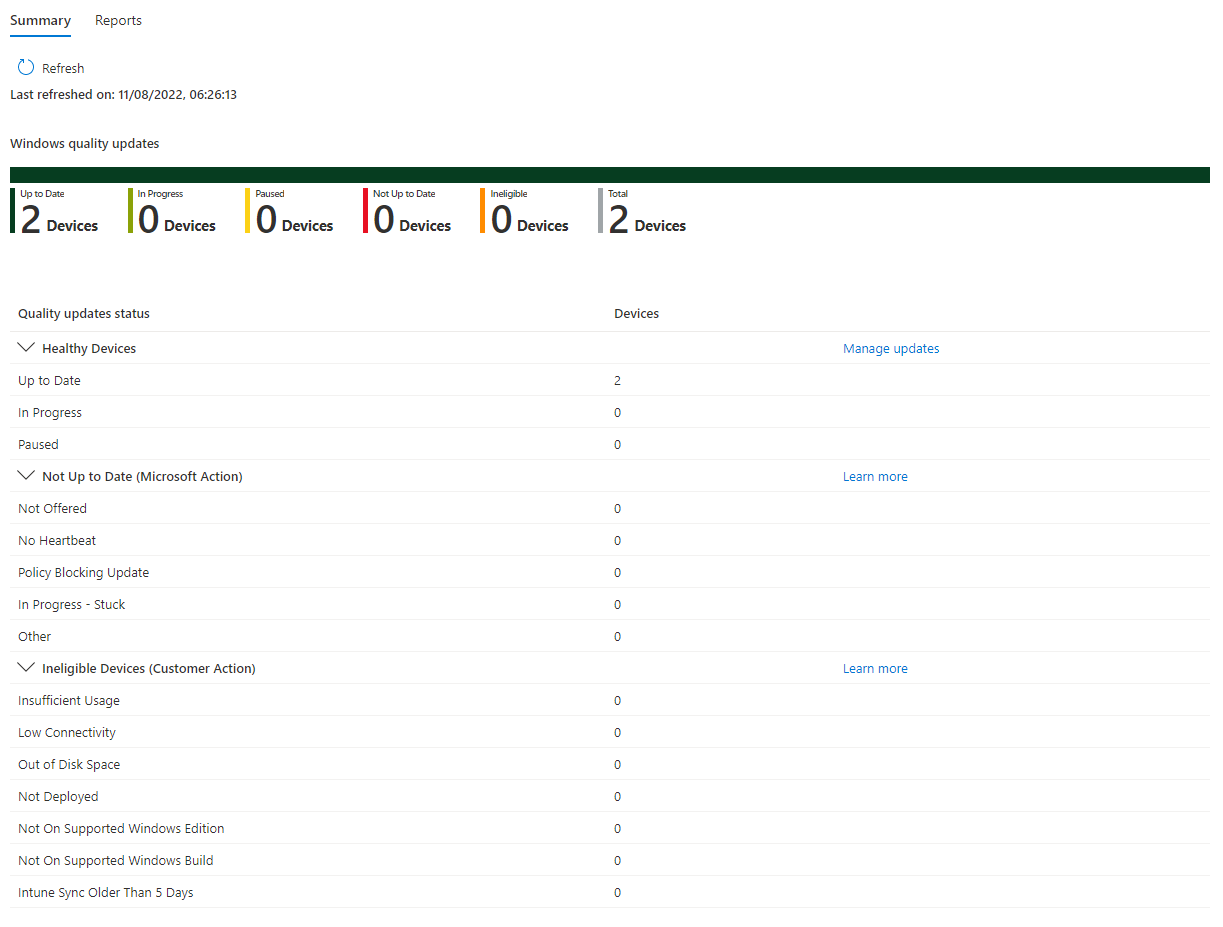
Overall the reporting does feel a little lacking - of the two reports which relate to updates, only one is specific to Autopatch registered devices, and they are both in preview. I would like to see a big improvement in reporting for updates in general - not just Autopatch reporting - in Intune. Hopefully in the not too distant future, Microsoft will launch some much improved and comprehensive update reporting into the Intune portal.
Further Reading
In this post
- Introduction
- Pre-requisites
- Enrolling
- Registering Devices
- What does it do in the backend?
- Reporting
- Further Reading
Support My Work
I hope you find my content useful. Please consider tipping to support the running costs of hosting, licensing etc on my Ko-fi page.

