Active Directory: Recovering Deleted Items
A while ago we accidentally deleted a leaving staff member's account instead of disabling it - and pure bad luck means this particular member of staff came back a week later to cover a staff illness. Not wanting to have to re-create the account I discovered that the Active Directory Recycle Bin had not been enabled in the forest - oh no! Luckily we can still get the account back. Objects deleted in AD are tombstoned for 180 days (by default).
Tombstone Reanimation
When you delete an object in AD it is moved to the Deleted Objects container and hidden from view. To get the object back, we need to move it back from the Deleted Objects container and take off the isDeleted flag. The old way to do this was complicated using ldp.exe and, at least on my test domain, doesn't work claiming the object I am trying to restore doesn't exist (despite it showing it on screen) - although it did work on my production environment.
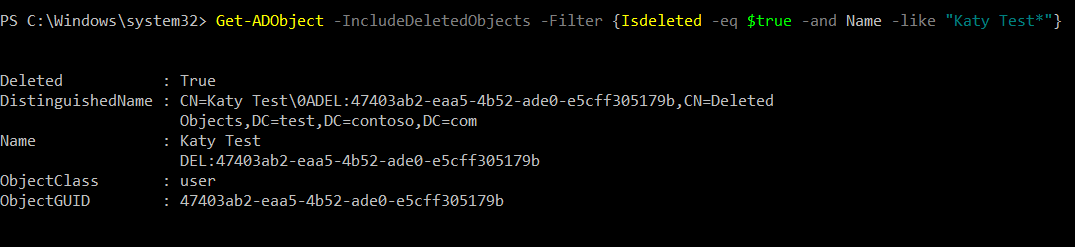
From an elevated PowerShell window, run Get-ADObject -IncludeDeletedObjects -Filter {IsDeleted -eq $true}. This will show you everything that is hanging about in the Deleted Objects container. You can further filter this with Get-ADObject -IncludeDeletedObjects -Filter {Isdeleted -eq $true -and Name -like "Katy Test*"}
Note you'll need the wildcard at the end as the object is renamed in the form of "Katy Test\0ADEL:guid". The \0A displays as a new line in PowerShell.
Once you've got the ObjectGUID or DistinguishedName of the object you wish to restore, run Restore-ADObject -Identity "GUID or DistingushedName here" -NewName "Katy Test". You have to specify -NewName. Optionally you can specify -TargetPath if you want to restore to an alternative location - this is the DN to the location, e.g. CN=Users,DC=contoso,DC=com.
The recovered object needs to be enabled and given a password, and you'll notice it has been stripped of nearly all its attributes. It'll be a member of Domain Users and have a Pre-Win2000 Logon Name, that's about it. However the most important bit is that it keeps the original SID so any NTFS permissions referencing it will still be valid and not need updating.
Enabling the Recycle Bin
It's much, much easier if you have the Recycle Bin enabled before you accidentally delete a user. With the AD Recycle Bin you can restore the user with all its attributes from within a nice UI (the AD Admin Centre). You'll need Enterprise Admin (or Domain Admin in the forest root domain) rights as this turns it on for the forest. You also need your forest functional level to be 2008 R2 or higher.
Open the Active Directory Admin Centre, then click on your domain at the left. At the right hand side, click on Enable Recycle Bin... Give it a few seconds then refresh the window and you should see a Deleted Objects container appear.
Alternatively you can enable it using PowerShell:
Enable-ADOptionalFeature -Identity 'CN=Recycle Bin Feature,CN=Optional Features,CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=contoso,DC=com' -Scope ForestOrConfigurationSet -Target 'contoso.com'
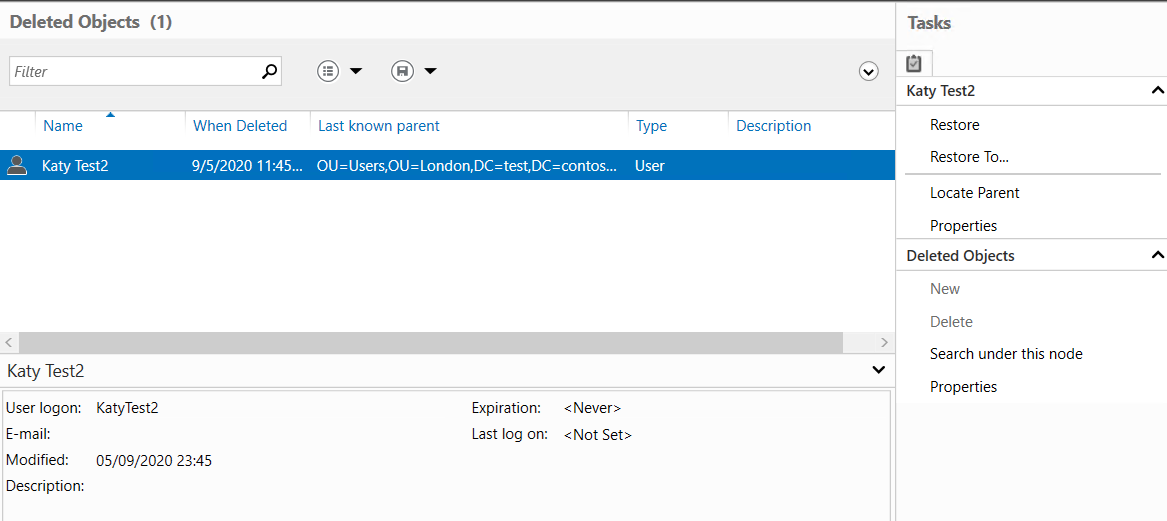
Restoring from the Recycle Bin
Now you've got the Recycle Bin enabled, anything you delete will show up in Deleted Objects within the AD Admin Centre. From here you can simply click the object, then click Restore. This will bring the user back with all their attributes, and even their password, intact.
You can also use the same PowerShell cmdlets detailed earlier on in this post to restore items from the Recycle Bin with all their attributes intact.