Hybrid Azure AD Domain Join using Client-side targeting
The standard method to configure hybrid domain join is to open up Azure AD Connector and follow the wizard. However this isn't suitable for every environment - for a start it needs to write forest-level configuration data, create a Service Connection Point (SCP), and if you want to link multiple tenancies to a single AD forest you're in for a hard time.
Luckily we can hybrid join with some registry settings on the client devices, and don't need to set up the forest level SCP. Here's how I've managed it on my network.
As a prerequisite you'll need AzureAD Connect running and synchronising your users and computers. I'll assume you've already done this step, if not there should be plenty of guides about on the Internet.
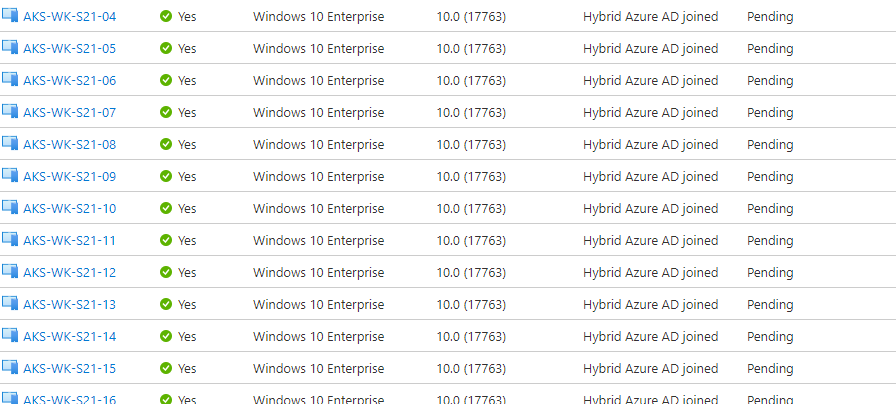
If you take a look at the Azure AD portal and click on Devices you should notice all your devices sat there with a status of "Pending", and going off the version number have been sat there quite a while.
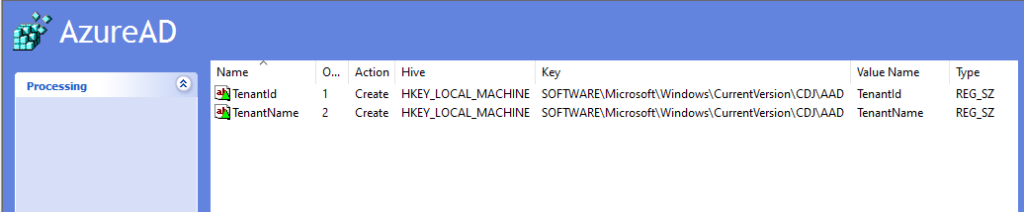
You will need to create two registry settings on each computer - easiest way to do this is probably a Group Policy Preferences Registry item. Create two settings:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD\TenantId - REG_SZ - and set the value to your tenant ID (can be obtained from the Azure AD Overview screen)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD\TenantName - REG_SZ - and set the value to your primary domain (again this can be seen on the Azure AD Overview screen).
Now on a test device, open an elevated command prompt (or elevated PowerShell) and run:
gpupdate
to allow the policy to apply the registry changes to the device, and then:
dsregcmd /join
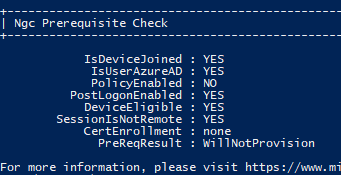
This will take a few seconds and hopefully will complete with no problems. You can then run dsregcmd /status to see the status, or refresh the browser window in Azure AD -> Devices.
You don't need to run dsregcmd /join on every device, if you wait long enough they will join by themselves. If you don't want to wait, just run dsregcmd /join on each device using a Config Mgr Powershell script or other remote execution tool.
Device Collection for Config Mgr
If you want a device collection showing your hybrid joined devices in Config Mgr then use the following query:
select SMS_R_System.ResourceId, SMS_R_System.ResourceType, SMS_R_System.Name,
SMS_R_System.SMSUniqueIdentifier, SMS_R_System.ResourceDomainORWorkgroup, SMS_R_System.Client from SMS_R_System
inner join SMS_Client_ComanagementState on SMS_Client_ComanagementState.ResourceId = SMS_R_System.ResourceId
where SMS_Client_ComanagementState.HybridAADJoined = 1
BitLocker Recovery Keys
Now your devices are hybrid joined, their BitLocker recovery keys can be stored in Azure AD. To do this run the following PowerShell script on each device (e.g. through Config Mgr Scripts):
$KeyProtectors = (Get-BitlockerVolume -MountPoint $env:systemdrive).KeyProtector
BackupToAAD-BitLockerKeyProtector $env:systemdrive -KeyProtectorId ($KeyProtectors | Where-Object { $_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorID
