Powershell Remoting
I recently discovered one of my deployment scripts does not work on Win 10 1809 any more (it ran dism to install the dot Net Framework 3.5 - just errors out) however that the powershell version (Add-WindowsCapability) works fine. Had to get this rolled out to a handful of PCs ASAP in order for a legacy application to successfully run. As time was of the essence, I ended up running round the 24 PCs like an idiot, logging on and running the command, but I thought "Why don't I just enable PS Remoting, then I could at least do this from my desk scripted". Obviously the ideal solution would be to deploy the Netfx3 install via SCCM but PS Remoting will still be handy.
Update: I've since added .net35 as a step in the MDT/Config Mgr task sequence "install windows features". Another way of pushing out .net35 to existing PCs would be using "Run Script" in Config Mgr. I don't think my version of Config Mgr had that feature when I originally wrote this blog. So first thing was to edit the "Computer Settings" GPO I have:
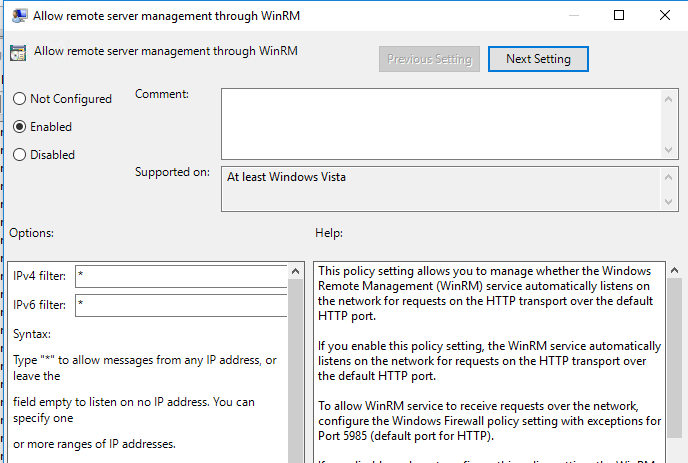
So the first thing we want to do is enable the WinRM Service. To do this we go to: Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Remote Management (WinRM) -> WinRM Service and enable the first policy, "Allow remote server management through WinRM". Now if you don't read the entire of the description at the right, and only go off what you see on the left hand side, it appears that this is where you tell it what PCs you want to allow remoting from. Nope! This actually tells it which interfaces to listen on. "Accept messages from these IPs" is not very clear, I got caught out by this and spent a while trying to work out why it would only work when the remote PC was on the same subnet as my PC. So we'll stick * into IPv4 and IPv6 so that it binds to all interfaces. Don't worry if you want to restrict what can connect as that's done in the next step.
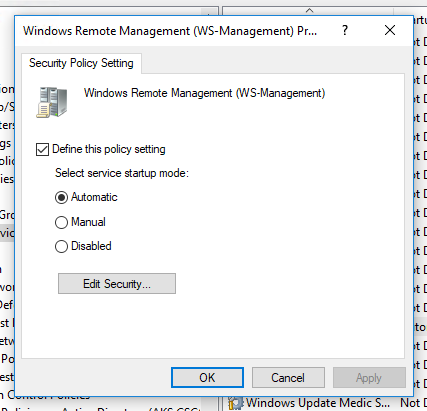
Step 2 is to make sure the service is actually going to run. Go to: Computer Configuration -> Policies -> Windows Settings -> Security Settings -> System Services and find "Windows Remote Management (WS-Management)". Edit this setting and set the service to Automatic start up.
Next we want to add the firewall rule, so go to: Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Defender Firewall -> Windows Defender Firewall -> Inbound Rules. Add a new rule: Rule Type: Predefined -> Windows Remote Management. Complete the wizard, then go into the rule's properties and onto the Scope tab.
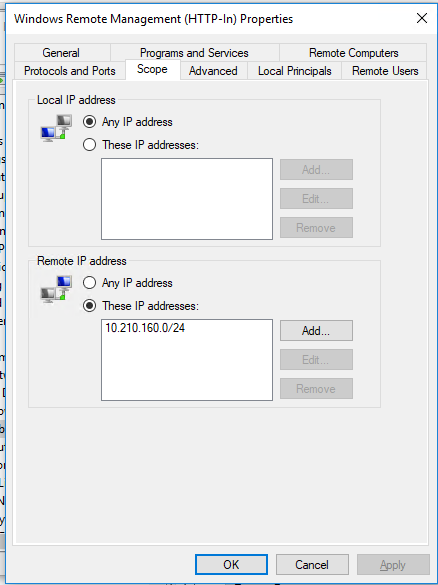
Enter the IP range/subnets that you wish to be able to access this PC remotely, and press OK. I've added my management PC subnet in here. Once the policy refresh has taken place, you should be able to enter remote powershell sessions on your clients. It may take a restart for the service changes to take affect.
To connect to a session, simply run:
New-PSSession -Computer remotepcname -Credential domain\adminuser | Enter-PSSession
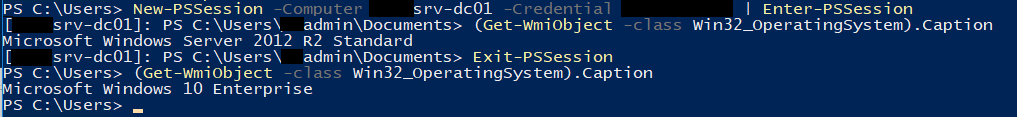
Your prompt will change to show that you are connected to a remote session. To disconnect, type Exit-PSSession. This will exit, but not remove, the session. To remove the session you will need to run Get-PSSession, note down the session ID and feed it into Remove-PSSession. I've not found a way to run anything remotely that requires elevation - for testing some changes I had made to other policies I was attempting to run Invoke-GPUpdate within a Remote PS session to my DC, but that failed as Invoke-GPUpdate requires elevation.

